Chip-Off Digital Forensics
Chip-Off Forensics
The raw data of the solid state memory chips found in thumb drives, memory cards, mobile phones, tablets, and other smart devices can contain crucial information you won’t find anywhere else on the device. But they may not be acquirable through non-invasive digital forensics methods – rather, the device must be opened up and the chip removed for data extraction, hence the word “chip-off.” This is especially true if the device has sustained severe physical damage. Removing the individual flash memory chips and acquiring them in a chip-off forensics procedure may be your only way to get a complete picture of the device’s usage.
Gillware offers chip-off forensics services for forensic investigators and others who may need this service. Chip-off forensics is an invasive forensic acquisition technique. Chip-off computer forensics requires specialized tools and experts to safely remove the chips, create forensic images of their contents, and properly realign their contents into coherent data. The flash media and mobile device forensics experts at Gillware have the skills, experience, and tools needed to safely perform these chip-off forensic operations.
Physical Forensic Acquisition
In the world of mobile device forensics, there are several levels of data acquisition. The higher levels, such as logical and file system acquisition, may only scratch the surface of the device’s data storage. In some situations, these levels may be sufficient for your investigation, or they may be the only possible levels of acquisition. In other situations, a deeper level of data acquisition, if possible, may reveal even more about the device and its user.
Physical acquisition is the lowest and deepest level of data acquisition. There are non-invasive ways to physically acquire a storage device or smart device, but especially in the case of smart devices, these non-invasive methods may not always work. In some cases, smartphones may not be physically acquirable by readily available forensic tools such as Cellebrite or by JTAG data extraction. In other cases, the device may be too damaged for non-invasive means of physical data acquisition to prove successful.
For other devices relying on flash memory chips to store data, such as solid state drives (SSDs), USB thumb drives, and Secure Digital (SD and microSD) memory cards, chip-off forensic analysis may be necessary if the devices are physically damaged, or if the devices have been formatted or data has been deleted and has become irretrievable by other means.
Like any other forensic technique, chip-off doesn’t have a 100% success rate. For example, if the device is encrypted, as many smartphones today are, physical acquisition will not offer a “backdoor” to the data contained within. Under these circumstances, finding a way to acquire data via the higher levels will prove more fruitful to investigators.
Physically Acquiring a Device with Chip-Off Forensics
As the word suggests, chip-off forensics requires removal of the flash memory chip (or chips) containing the device’s data. SD cards, thumb drives, and SSDs have one or more NAND or NOR flash memory chips. Mobile phones and other smart devices contain flash memory, which can be in the form of NAND, NOR, eMMC (embedded multimedia memory card), or UFS chips.
These chips are held onto the device’s circuit board, usually by a very strong epoxy. A skilled electrical engineer must free the chips by desoldering them off of the board and cleaning or sanding off the epoxy in order to access the chip. This is a difficult and delicate procedure, and if performed incorrectly, the flash memory chips can become damaged, making it impossible for an investigator to acquire their contents.
Making sense of the contents of the flash memory chips after physically acquiring it can be a challenge, depending on the type of flash memory used. The raw memory dump from a NAND memory chip, for example, in no way resembles the contents of the device at first. Elements of the chip’s flash translation layer and other maintenance algorithms must be stripped away in order to piece the relevant data together. When a flash device such as a USB thumb drive or SSD operates normally, its controller performs this task and reassembles the data on the fly. The eMMC flash memory chip usually found in phones and some tablets, on the other hand, has a controller built into it, so reassembling the data pulled from these memory chips requires much less intensive work.
SSD, Memory Card and USB Thumb Drive Chip-Off Forensics
Chip-off forensics is generally useful when a device has been too damaged to function. SD memory cards and USB thumb drives, due to their small size, can easily suffer severe damage. In certain situations, the data on failed SSDs may also require chip-off methods to physically acquire. However, there are also situations in which a chip-off recovery must be done on a perfectly healthy device.
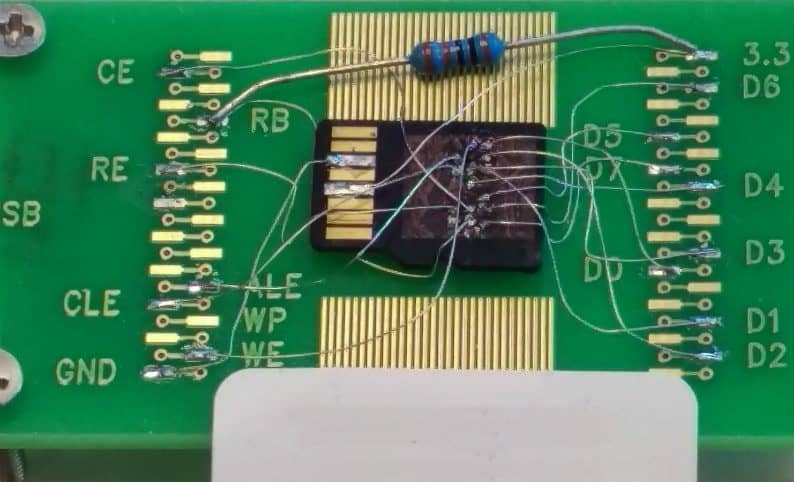
Even if a flash memory card or thumb drive retrieved as part of your investigation is perfectly healthy, circumstances may require you to physically acquire the chip’s contents using chip-off methods. NAND flash memory maintenance algorithms, such as TRIM, wear leveling, and garbage collection protocols, can make these devices appear to be blank on a logical level after they have been reformatted or had data deleted from them. Even if a memory card shows you all zeroes when you look at its sectors in a hex editor, important data may still live on its NAND chip on the physical level.
Many USB thumb drives and SD cards make use of monolithic flash memory chips. These chips are extremely difficult to acquire because rather than featuring all parts of the device as discrete components, the NAND flash memory itself has been soldered together with the controller, circuit board, and USB or memory card interface into a nigh-impenetrable package.
In order to acquire the contents of these monolithic flash memory chips, our flash memory forensics experts must connect tiny leads to very specific contact points on the monolithic package’s hidden ball grid array, in a process we call “spiderwebbing”.
Mobile Phone Chip-Off Forensics
Mobile devices, tablets, and other smart devices generally have a flash memory chip connected directly to their motherboards and a SIM card, and often will have a removable microSD card for data storage as well. In mobile forensics, all storage media should be acquired to paint a full forensic picture. Circumstances may require chip-off analysis of one or more of the storage media within a smart device.
Our engineers can use chip-off forensic techniques to physically acquire the data stored on a mobile phone’s NAND, NOR, eMMC, or eMPC flash memory chip. We can also successfully conduct chip-off investigations of mobile devices containing UFS chips as well, such as Samsung Galaxy S7 smart phones.
Chip-Off Forensics for Severely Damaged Mobile Devices
While JTAG forensics can allow a forensic investigator to obtain a physical acquisition of a mobile device when it has suffered minor damage that prevents other non-invasive forms of physical acquisition, it requires the device to be functional. At the very least, it must power on. If the smartphone has suffered severe physical damage and is entirely non-functional, the only way to acquire data from the device may be to remove and image the device’s flash memory chips.
In chip-off forensics situations such as this, Gillware can leverage the experience of the mobile phone data recovery experts in Gillware’s secure, world-class data recovery lab. Our data recovery experts have years of experience using chip-off methods to salvage data from severely damaged Android and iOS phones and other smart devices. Devices that have seen water damage, fire damage, and other forms of excessive physical trauma, can still have data salvaged off of their flash memory chips.
In situations in which a mobile device has sustained severe damage, sometimes a complete forensic image of the device’s contents may not always be possible. As resilient as solid state memory is, these chips can still become damaged to the point where some of their contents cannot be retrieved. Gillware’s forensics experts, with their experience in salvaging data from failed devices, are adept at working their way around the blank spots that can result from an incomplete forensic image in order to uncover whatever meaningful data might still be there.