Nemucod Data Recovery: Recovering Data from Ransomware
There’s a lot of malicious software in the world, of varying degrees of nastiness. But ransomware is by far one of the nastiest types of malware on the planet. There are legions of variations, each newer version improving on the last to make circumventing their encryption more difficult—or impossible. In this data recovery case, a client was hit with the Nemucod ransomware virus. This virus infects the hard drives of Windows machines and downloads a malware-ridden payload to the victim’s computer. As of this spring, that payload also includes a nasty virus that encrypts the victim’s critical documents. The virus tags the affected files with the “.CRYPTED” file extension and renders them unusable. The client brought their hard drive to us in the hopes that our data recovery experts could successfully perform a Nemucod data recovery service.
Nemucod Data Recovery Case Study: Recovering Data from Ransomware
Drive Brand: Samsung ST1000LM024
Drive Capacity: 1 TB
Operating System: Windows
Situation: Nemucod ransomware encrypted and added “.CRYPTED” extension to all important files
Recovery Data Needed: Business documents
Binary Read: 100%
Gillware Data Recovery Case Rating: 10
Nemucod Ransomware: An Overview
The Nemucod virus is a relatively young virus. According to the databases of antivirus tools such as McAfee and Symantec, it first appeared around December 2015. Nemucod currently only affects Windows computers. Nemucod often appears in the guise of a Javascript email attachment. When an unwitting victim downloads the attachment, which may claim to be a business invoice or legal summons, they end up running the JScript file containing the virus.
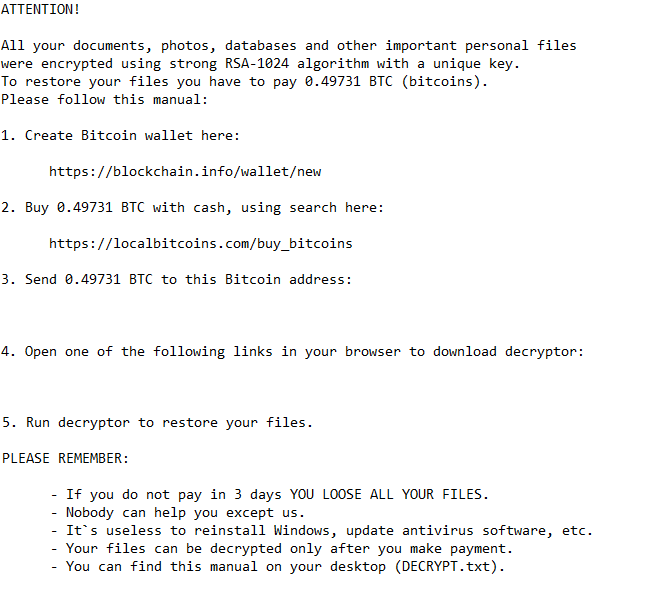
Initially, Nemucod would simply download a malware-ridden payload to deposit even more viruses on the victim’s computer. However, in the spring of 2016, a new version of Nemucod began to encrypt user documents as well. The virus would hold the victim’s files for ransom, offering the decryption key in exchange for 0.4 to 0.6 Bitcoins (an untraceable, digital crypto-currency).
The newest version of Nemucod uses some clever tricks to circumvent any types of firewall or Internet connection settings that might prevent it from downloading and running its toxic ransomware payload. There is no doubt that its creators are very sly. But like most sly characters, they thought they could get away with taking some shortcuts. It just so happened that Nemucod’s creators chose to cut corners when it came to Nemucod’s ransomware payload.
Nemucod’s designers claim to use RSA 1024, 2048, or 4096-bit encryption to ransom its victim’s files. But research has shown that it actually uses much simpler XOR encryption. Ultimately, this was one of Nemucod’s fatal flaws. By cutting corners like this, it left a chink in the ransomware’s armor. By exploiting this weakness, our logical and forensic data recovery expert Cody could recover our client’s critical files. In this Nemucod data recovery case, the client would not have to pay the bad guys to get their files back.
The Nemucod Data Recovery Process
There is one tool already out there to help victims of the Nemucod ransomware virus. A free decryptor takes advantage of the virus’ weak encryption. The decryptor program, if fed one encrypted file and an unencrypted version of the same file, can reverse-engineer the decryption key for all of the affected files. Of course, this relies on the victim having an unencrypted version of one of their affected files on hand. In this Nemucod data recovery case, our client did not. So it was up to us to find one for them.
Fortunately for our client, we have expert logical and forensic data recovery technicians like Cody on our side. And we have our forensic analysis tool, HOMBRE, at our disposal. Cody’s goal was to scour the unallocated portions of the disk with HOMBRE. In the vast unallocated wasteland making up the bulk of this 1 TB Samsung drive, Cody hoped to find deleted versions of the encrypted files, using some of the same techniques that make deleted data recovery possible. Even just one file would do. With all of HOMBRE’s tools at his fingertips, this was much easier than finding a needle in a haystack.
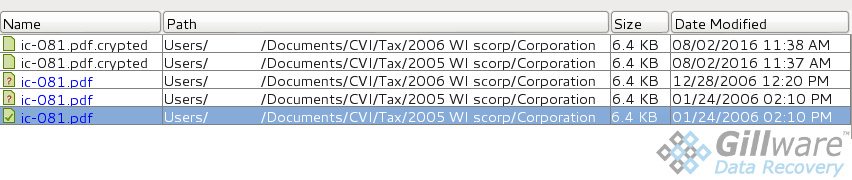
In the above image, the file names listed in black are the current versions of one of the client’s critical files. The Nemucod virus appends the “.CRYPTED” extension to every file it encrypts. You can see by the “Date Modified” field that the virus hit the client on August 2. The blue files are deleted versions of the same file that Cody turned up in his logical analysis. The ones with question marks were too logically damaged to be useful (as shown by question mark icons). But one deleted file was completely intact. Cody had found our key to Nemucod’s digital padlock.
Conclusion
After restoring the deleted file, Cody could use the Emisoft decryptor tool to generate a decryption key. The process went off without a hitch. The decryption key worked for each and every of the client’s encrypted files. This ransomware data recovery case turned out to be a great success. We rated this Nemucod data recovery case study a 10 on our ten-point data recovery case rating scale.
Every ransomware virus works just a little differently. There’s no one-size-fits-all approach to ransomware data recovery. In some instances, circumventing the encryption might just not be possible. If you’ve been hit with a ransomware virus, Gillware is here to help!.
