An In-Depth Look at Ransomware
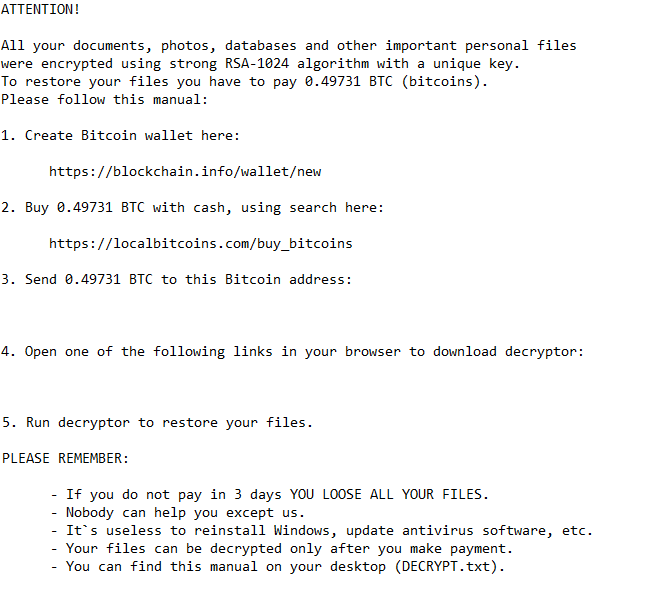
What is Ransomware?
Ransomware is malware that is created for the express purpose of making a profit, traditionally via extorting its victims. There are many types of ransomware, but by far the two most popular types are locker ransomware and crypto ransomware. Though they function slightly differently, the end goal is the same.
Locker ransomware restricts access to the user’s device until they pay the ransom. This means when the locker ransomware is launched, nearly all computer functionality is locked down, excluding the use of any functions necessary for payment. Fortunately, locker ransomware is typically easier to bypass since it doesn’t affect the system or files in any permanently damaging way.
Crypto ransomware, on the other hand, works by first going through and either encrypting or deleting all the important files it can find, including any local backups. If you don’t pay the ransom within a preset period of time, the creator will not provide you with a decryption key and your files will be permanently encrypted, which in this case is just as good as destroyed. If you don’t know much about encryption, here’s an article to explain how symmetric and asymmetric encryption work.
Fun fact: In order to ‘brute-force’ (go through numbers until you find the right one) the decryption key for a symmetric AES 256-bit key, it would take 50 supercomputers capable of trying a billion, billion AES keys every second roughly 3×10^51 years to try all possible combinations. To find the key, they would really only need to get through about half, but that’s still a pretty long time. For more information on how Gillware recovers data in ransomware situations, please view the webinar for an in-depth discussion in addition to multiple case studies for some real world examples.
How Much Do Ransomware Attacks Cost?
The average ransom is around $300 USD, though this can vary depending on how targeted the attack is. Since 2013 when crypto ransomware re-entered the scene, we’ve seen an increase in the sophistication of certain ransomware attacks, most recently seen in the widely-publicized extortion of a hospital for thousands of dollars.
Though much more effective in their ability to generate large profits, these targeted attacks are in the minority, as most attacks are executed randomly and can only demand small sums if they expect to be paid.
The amount of productivity lost also typically costs thousands of dollars, in addition to the cost of any files or backups lost. All in all, it isn’t surprising that ransomware attacks collectively cost tens of millions of dollars every year.
Why has Ransomware Become So Successful?
Since the return of ransomware, it has seen great success and subsequent ubiquity due to three factors: improved technology, better distribution strategies, and simpler monetization.
Improved technologies include stronger encryption in addition to higher performance computers and servers. The stronger encryption makes it either more difficult or impossible to work around, while better computers and servers means it is now more feasible to encrypt all of someone’s important files in a relatively small amount of time (before they notice).
In terms of better distribution strategies, it is now easier to attack people as well as easier to get away with. The first way it is easier is due to ‘bring-your-own-device’ weaknesses. This happens when someone brings their laptop/tablet/smartphone away from work, connects to some other network without a firewall (home), clicks something suspicious and unknowingly gets the ransomware, then brings their device back to work. Since the firewall is designed to target only external threats, the ransomware is able to infect the business network and target important file types as well as any onsite backups. After a period of dormancy, the ransomware will begin encrypting files and deleting backups as quickly as it can.
Another great advantage in terms of distribution strategies is the advent of anonymous web browsing via software like the Tor Browser. By using things like Tor, it is very easy to conceal the origin of these attacks and thus put ransomware out into the world without fear of being caught.
Simpler monetization is the final reason we have seen many more ransomware attacks in recent years. Earlier attacks would disguise themselves as either authority figures or helpful software (antivirus) in an attempt to get victims to pay. More recent ransomware has ditched these techniques after finding that outright stating the malicious intent of the ransomware is far more effective at scaring victims into paying, not to mention the fact that there’s no need for social engineering when your encryption is nigh impossible to bypass.
They also no longer need to fret about how they will be paid, as anonymous cryptocurrencies such as Bitcoin make it much easier for these transactions to take place without being traced.
How Can You Protect Yourself and Your Clients from Ransomware?
We’ve compiled a small list of recommendations to get you started. By taking these ten basic precautions, you will greatly lower the risk of infection and data loss.
- Remove administrative privileges where they are not needed
- Educate your customers about potentially dangerous emails and links
- Improve customer email spam filters
- Store local backup on a machine whose sole purpose is storing local backups
- Only allow backup administrator access to the local backup machine
- Protect the local backup machine with a firewall from internal and external threats
- Offer a full network audit to understand users and permissions to prevent future infections
- Offer an offsite backup solution with revisions to restore from in the event of an infection
- Have clients sign waivers if they choose to forgo either option in order to protect yourself in the event of an infection
- Be sure to implement these practices in your own business, as you could be the one bringing the infection into your clients’ businesses
